SpringBoot 로 JWT 토큰 생성 및 해석하기
JWT 라이브러리
build.gradle
// jwt
implementation 'io.jsonwebtoken:jjwt-api:0.12.3'
runtimeOnly 'io.jsonwebtoken:jjwt-impl:0.12.3'
runtimeOnly 'io.jsonwebtoken:jjwt-jackson:0.12.3'
Plain Text
복사
프로젝트 구조
작업 코드
1.
build.gradle
2.
application.properties
3.
SecurityConfig.java
4.
SecurityConatants.java
5.
JwtProps.java
6.
AuthenticationRequest.java
7.
LoginController.java
build.gradle
plugins {
id 'java'
id 'war'
id 'org.springframework.boot' version '2.7.17'
id 'io.spring.dependency-management' version '1.1.4'
}
group = 'com.joeun'
version = '0.0.1-SNAPSHOT'
java {
sourceCompatibility = '11'
}
configurations {
compileOnly {
extendsFrom annotationProcessor
}
}
repositories {
mavenCentral()
}
dependencies {
implementation 'org.springframework.boot:spring-boot-starter-security'
implementation 'org.springframework.boot:spring-boot-starter-web'
compileOnly 'org.projectlombok:lombok'
developmentOnly 'org.springframework.boot:spring-boot-devtools'
annotationProcessor 'org.projectlombok:lombok'
providedRuntime 'org.springframework.boot:spring-boot-starter-tomcat'
testImplementation 'org.springframework.boot:spring-boot-starter-test'
testImplementation 'org.springframework.security:spring-security-test'
// spring-boot-configuration-processor
implementation 'org.springframework.boot:spring-boot-configuration-processor'
// jwt
implementation 'io.jsonwebtoken:jjwt-api:0.12.3'
runtimeOnly 'io.jsonwebtoken:jjwt-impl:0.12.3'
runtimeOnly 'io.jsonwebtoken:jjwt-jackson:0.12.3'
}
tasks.named('test') {
useJUnitPlatform()
}
Plain Text
복사
application.properties
# HS512 알고리즘의 시크릿키 : 512비트 (64바이트) 이상
# https://passwords-generator.org/kr/
# ✅ 위 사이트에서 길이:64 로 생성함.
com.joeun.jwt.secret-key=|+<T%0h;[G97|I$5Lr?h]}`8rUX.7;0gw@bF<R/|"-U0n:_6j={'.T'GHs~<AxU9
Plain Text
복사
참조 - 알고리즘 시크릿키 생성 사이트
SecurityConfig.java
package com.joeun.jwt.config;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.configuration.EnableWebSecurity;
import org.springframework.security.config.http.SessionCreationPolicy;
import org.springframework.security.web.SecurityFilterChain;
// TODO : deprecated 없애기 (version : before SpringSecurity 5.4 ⬇)
// @EnableWebSecurity
// public class SecurityConfig extends WebSecurityConfigurerAdapter {
// OK : (version : after SpringSecurity 5.4 ⬆)
@Configuration
@EnableWebSecurity
public class SecurityConfig {
// OK : (version : after SpringSecurity 5.4 ⬆)
@Bean
public SecurityFilterChain securityFilterChain(HttpSecurity http) throws Exception {
// 폼 기반 로그인 비활성화
http.formLogin(login ->login.disable());
// HTTP 기본 인증 비활성화
http.httpBasic(basic ->basic.disable());
// CSRF(Cross-Site Request Forgery) 공격 방어 기능 비활성화
http.csrf(csrf ->csrf.disable());
// 세션 관리 정책 설정: STATELESS로 설정하면 서버는 세션을 생성하지 않음
// 🔐 세션을 사용하여 인증하지 않고, JWT 를 사용하여 인증하기 때문에, 세션 불필요
http.sessionManagement(management ->management
.sessionCreationPolicy(SessionCreationPolicy.STATELESS));
// 구성이 완료된 SecurityFilterChain을 반환합니다.
return http.build();
}
// TODO : deprecated 없애기 (version : before SpringSecurity 5.4 ⬇)
// @Override
// protected void configure(HttpSecurity http) throws Exception {
// // 폼 기반 로그인 비활성화
// http.formLogin().disable()
// // HTTP 기본 인증 비활성화
// .httpBasic().disable();
// // CSRF(Cross-Site Request Forgery) 공격 방어 기능 비활성화
// http.csrf().disable();
// // 세션 관리 정책 설정: STATELESS로 설정하면 서버는 세션을 생성하지 않음
// // 🔐 세션을 사용하여 인증하지 않고, JWT 를 사용하여 인증하기 때문에, 세션 불필요
// http.sessionManagement()
// .sessionCreationPolicy(SessionCreationPolicy.STATELESS);
// }
}
Java
복사
SecurityConatants.java
package com.joeun.jwt.constants;
// 해당 클래스는 Spring Security 및 JWT 관련 상수를 정의한 상수 클래스입니다.
/**
* HTTP
* headers : {
* Authorization : Bearer ${jwt}
* }
*/
public final class SecurityConstants {
// JWT 토큰을 HTTP 헤더에서 식별하는 데 사용되는 헤더 이름
public static final String TOKEN_HEADER = "Authorization";
// JWT 토큰의 접두사. 일반적으로 "Bearer " 다음에 실제 토큰이 옵니다.
public static final String TOKEN_PREFIX = "Bearer ";
// JWT 토큰의 타입을 나타내는 상수
public static final String TOKEN_TYPE = "JWT";
// 이 클래스를 final로 선언하여 상속을 방지하고, 상수만을 정의하도록 만듭니다.
}
Java
복사
JwtProps.java
package com.joeun.jwt.prop;
import org.springframework.boot.context.properties.ConfigurationProperties;
import org.springframework.stereotype.Component;
import lombok.Data;
// 해당 클래스는 Spring Boot의 `@ConfigurationProperties`
// 어노테이션을 사용하여, application.properties(속성 설정 파일) 로부터
// JWT 관련 프로퍼티를 관리하는 프로퍼티 클래스입니다.
@Data
@Component
@ConfigurationProperties("com.joeun.jwt") // com.joeun.jwt 경로 하위 속성들을 지정
public class JwtProps {
// com.joeun.jwt.secretKey로 지정된 프로퍼티 값을 주입받는 필드
// ✅ com.joeun.jwt.secret-key ➡ secretKey : {인코딩된 시크릿 키}
private String secretKey;
}
Java
복사
AuthenticationRequest.java
package com.joeun.jwt.domain;
import lombok.Getter;
import lombok.Setter;
import lombok.ToString;
@Getter
@Setter
@ToString
public class AuthenticationRequest {
private String username;
private String password;
}
Java
복사
LoginController.java
package com.joeun.jwt.controller;
import java.util.ArrayList;
import java.util.Date;
import java.util.List;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.http.HttpStatus;
import org.springframework.http.ResponseEntity;
import org.springframework.web.bind.annotation.GetMapping;
import org.springframework.web.bind.annotation.PostMapping;
import org.springframework.web.bind.annotation.RequestBody;
import org.springframework.web.bind.annotation.RequestHeader;
import org.springframework.web.bind.annotation.RestController;
import com.joeun.jwt.constants.SecurityConstants;
import com.joeun.jwt.domain.AuthenticationRequest;
import com.joeun.jwt.prop.JwtProps;
import io.jsonwebtoken.Claims;
import io.jsonwebtoken.Jws;
import io.jsonwebtoken.Jwts;
import io.jsonwebtoken.security.Keys; // 추가: 새로운 방식으로 SecretKey 생성을 위한 클래스
import lombok.extern.slf4j.Slf4j;
@Slf4j
@RestController
public class LoginController {
@Autowired
private JwtProps jwtProps;
/**
* 👩💼➡🔐 JWT 을 생성하는 Login 요청
* [GET] - /login
* body :
{
"username" : "joeun",
"password" : "123456"
}
* @param authReq
* @return
*/
@PostMapping("login")
public ResponseEntity<?> login(@RequestBody AuthenticationRequest authReq) {
// 사용자로부터 전달받은 인증 정보
String username = authReq.getUsername();
String password = authReq.getPassword();
log.info("username : " + username);
log.info("password : " + password);
// 사용자 역할 정보
List<String> roles = new ArrayList<>();
roles.add("ROLE_USER");
roles.add("ROLE_ADMIN");
// 서명에 사용할 키 생성 (새로운 방식)
String secretKey = jwtProps.getSecretKey();
byte[] signingKey = jwtProps.getSecretKey().getBytes();
log.info("secretKey : " + secretKey);
log.info("signingKey : " + signingKey);
// JWT 토큰 생성
String jwt = Jwts.builder()
.signWith(Keys.hmacShaKeyFor(signingKey), Jwts.SIG.HS512) // 서명에 사용할 키와 알고리즘 설정
// .setHeaderParam("typ", SecurityConstants.TOKEN_TYPE) // deprecated (version: before 1.0)
.header() // update (version : after 1.0)
.add("typ", SecurityConstants.TOKEN_TYPE) // 헤더 설정
.and()
.expiration(new Date(System.currentTimeMillis() + 864000000)) // 토큰 만료 시간 설정 (10일)
.claim("uid", username) // 클레임 설정: 사용자 아이디
.claim("rol", roles) // 클레임 설정: 역할 정보
.compact(); // 최종적으로 토큰 생성
log.info("jwt : " + jwt);
// 생성된 토큰을 클라이언트에게 반환
return new ResponseEntity<String>(jwt, HttpStatus.OK);
}
/**
* 🔐➡👩💼 JWT 를 해석하는 요청
*
* @param header
* @return
*/
@GetMapping("/user/info")
public ResponseEntity<String> userInfo(@RequestHeader(name="Authorization") String header) {
log.info("===== header =====");
log.info("Authorization : " + header);
String jwt = header.substring(7); // "Bearer " + jwt ➡ jwt 추출
log.info("jwt : " + jwt);
String secretKey = jwtProps.getSecretKey();
byte[] signingKey = jwtProps.getSecretKey().getBytes();
log.info("secretKey : " + secretKey);
log.info("signingKey : " + signingKey);
// TODO : deprecated 업애기 (version: before 1.0)
// Jws<Claims> parsedToken = Jwts.parser()
// .setSigningKey(signingKey)
// .build()
// .parseClaimsJws(jwt);
// OK : deprecated 된 코드 업데이트 (version : after 1.0)
// - setSigningKey(byte[]) ➡ verifyWith(SecretKey)
// - parseClaimsJws(CharSequence) ➡ parseSignedClaims(CharSequence)
Jws<Claims> parsedToken = Jwts.parser()
.verifyWith(Keys.hmacShaKeyFor(signingKey))
.build()
.parseSignedClaims(jwt);
log.info("parsedToken : " + parsedToken);
String username = parsedToken.getPayload().get("uid").toString();
log.info("username : " + username);
Claims claims = parsedToken.getPayload();
Object roles = claims.get("rol");
log.info("roles : " + roles);
return new ResponseEntity<String>(parsedToken.toString(), HttpStatus.OK);
}
}
Java
복사
Authorization 헤더
HTTP 요청에서 클라이언트가 서버에게 자신의 인증 정보를 제공하는 데 사용되는 헤더
Authorization: <type> <credentials>
Plain Text
복사
•
<type>: 인증 타입을 나타냅니다. 일반적으로 Basic 또는 Bearer가 사용됩니다.
◦
Basic: 클라이언트가 아이디와 비밀번호의 조합을 Base64로 인코딩한 값을 제공하는 경우 사용됩니다.
◦
Bearer: 토큰 기반의 인증에서 토큰을 나타냅니다.
•
<credentials>: 실제 인증 정보를 나타냅니다. 인코딩된 아이디와 비밀번호 또는 토큰이 여기에 들어갑니다.
예시
Authorization: Basic YWxhZGRpbjpvcGVuc2VzYW1l
Plain Text
복사
Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9...
Plain Text
복사
테스트
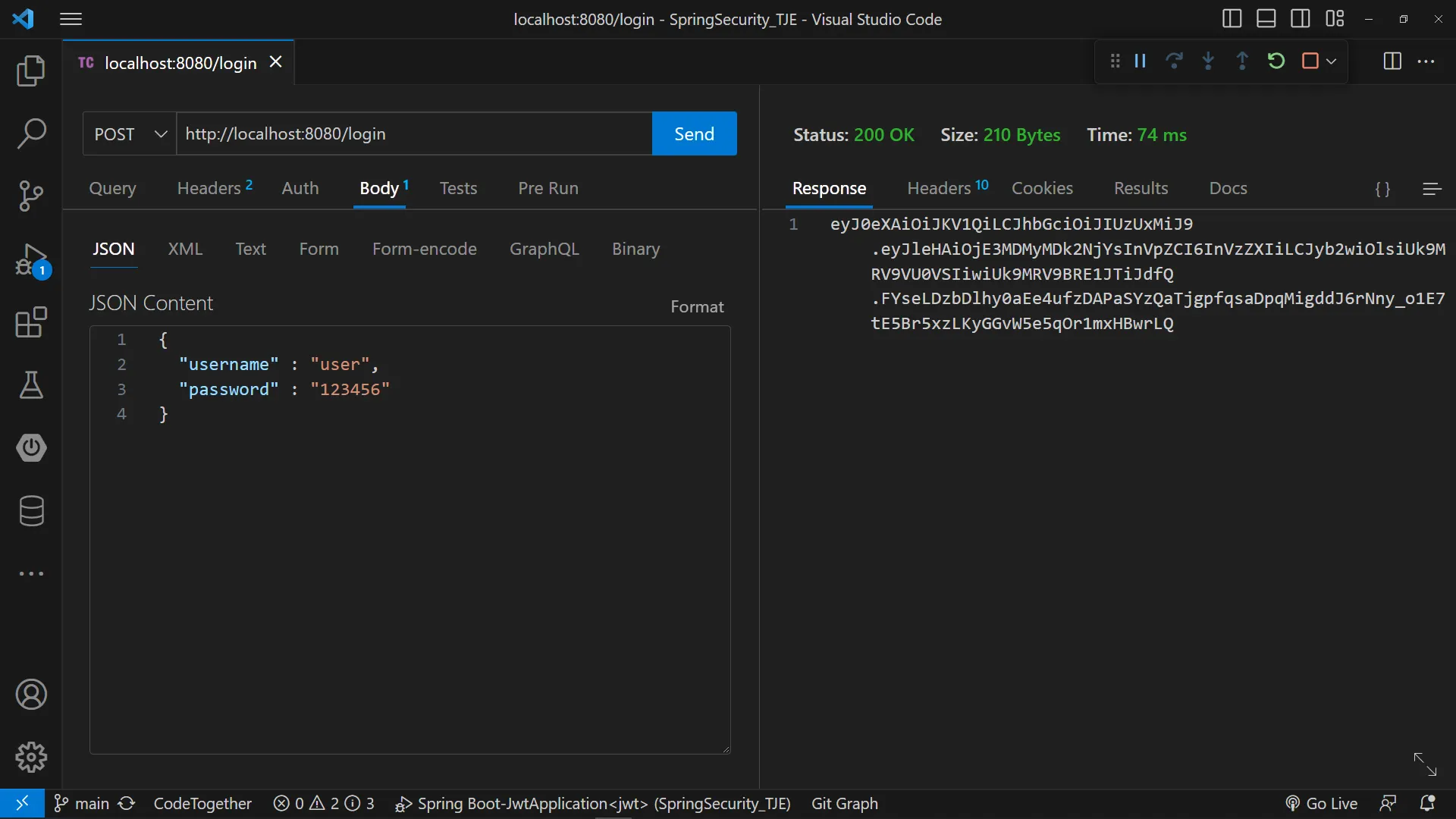
로그인 요청 (JWT 토큰 생성)
[POST] - /login
Request
•
•
body
{
"username" : "user",
"password" : "123456"
}
Java
복사
Response
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzUxMiJ9.eyJleHAiOjE3MDMyMDk2NjYsInVpZCI6InVzZXIiLCJyb2wiOlsiUk9MRV9VU0VSIiwiUk9MRV9BRE1JTiJdfQ.FYseLDzbDlhy0aEe4ufzDAPaSYzQaTjgpfqsaDpqMigddJ6rNny_o1E7tE5Br5xzLKyGGvW5e5qOr1mxHBwrLQ
Plain Text
복사
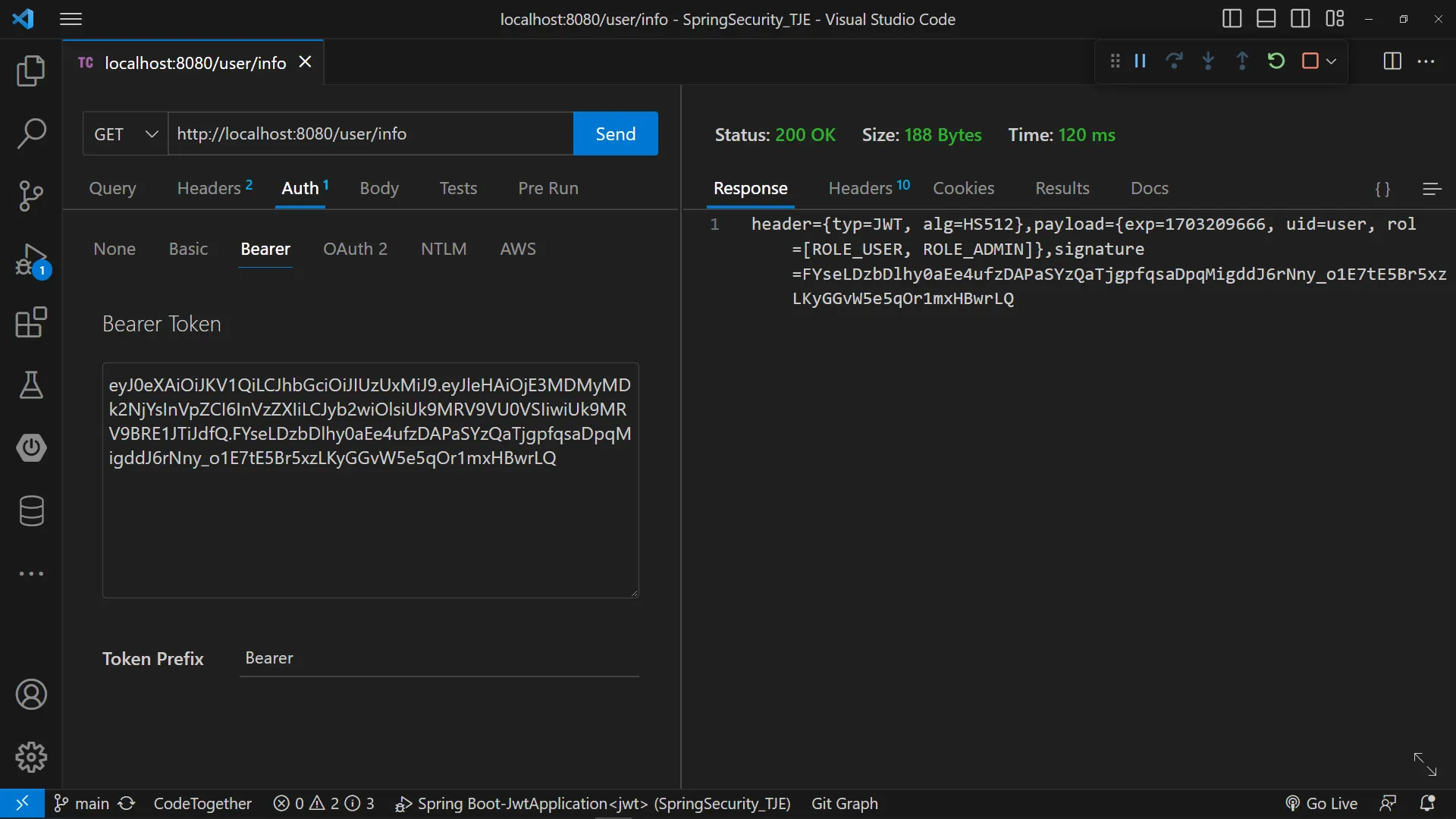
사용자 인증 및 권한 정보 확인 (JWT 토큰 해석)
[GET] - /user/info
Request
•
•
header
{
"Authorization" : "Bearer " + "eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzUxMiJ9.eyJleHAiOjE3MDMyMDk2NjYsInVpZCI6InVzZXIiLCJyb2wiOlsiUk9MRV9VU0VSIiwiUk9MRV9BRE1JTiJdfQ.FYseLDzbDlhy0aEe4ufzDAPaSYzQaTjgpfqsaDpqMigddJ6rNny_o1E7tE5Br5xzLKyGGvW5e5qOr1mxHBwrLQ"
}
Java
복사
Response
header={typ=JWT, alg=HS512},
payload={exp=1703209666, uid=user, rol=[ROLE_USER, ROLE_ADMIN]},
signature=FYseLDzbDlhy0aEe4ufzDAPaSYzQaTjgpfqsaDpqMigddJ6rNny_o1E7tE5Br5xzLKyGGvW5e5qOr1mxHBwrLQ
Plain Text
복사